Yulia Boychenko, journalist with the Mykolaiv-based online media outlet MykVisti, received a message that appeared to be an event invitation and contained a phishing link disguised as a registration form.
The journalist spoke about the incident with Kateryna Sereda, the Institute of Mass Information representative in Mykolaiv oblast.
On 13 October, the journalist received a message in Signal inviting her to a “closed charity party” in Kyiv. The message, screenshots of which the journalist shared, claims that the event is organized by the “Kyiv administration” and asks not to share the link to the registration form with anyone “for safety reasons.”
When Yulia asked what the event would be about, she was told that it would be attended by the Ukrainian Armed Forces commanders, NATO representatives, and top regional officials.
“As for the event, all the details are in the invitation, and, as per the event protocol, a person is supposed to learn the details on their own; I can only tell you that there will be top UAF commanders, several regional leaders, representatives of NATO charity foundations, and others present, I want to see you as an experienced journalist, because although the event is closed, it should be reported on after the fact,” the message says.
In order to access the journalist’s data, the malicious actors impersonated the Pershyi TV chief editor Viktor Medvid, using his photo and name.
The MykVisti team has contacted law enforcement bodies with a statement about the incident.
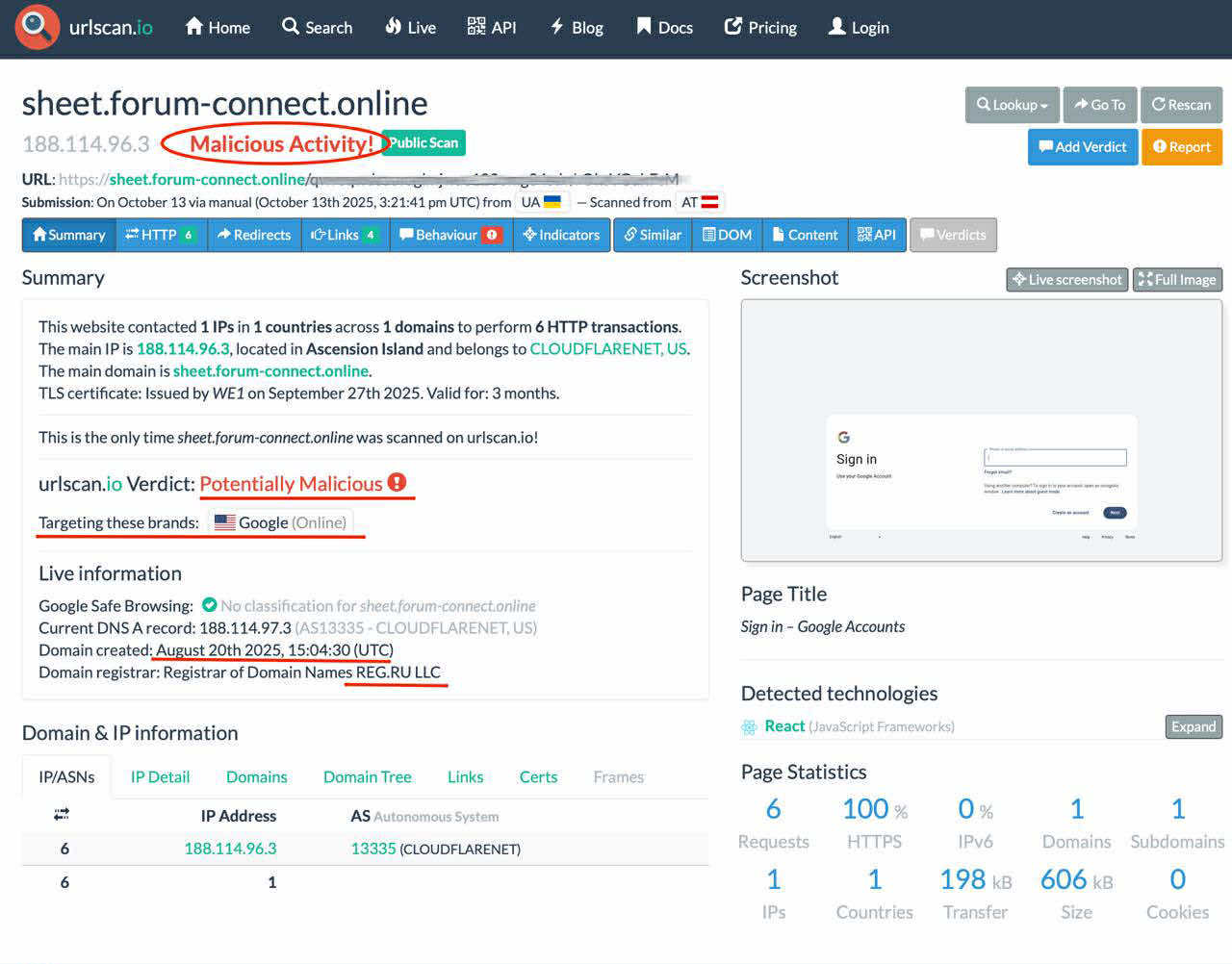
The link that was supposed to lead to a Google registration form turned out to be fake. The page mimicked an official Google service but opened on the forum-connect.online domain, registered in August 2025 through a Russian registrar and hidden by the proxy service Cloudflare.
An Urlscan check designated the link Potentially Malicious: the screenshot shows a clone of the Google login interface and the technical data suggests that the page loads external JavaScripts that process the entered data and may send it to third-party servers. The secure connection icon in the address bar here does not mean that the site is genuine: encryption only guarantees that the connection is encrypted, but does not confirm the authenticity of the resource’s owner.
The Institute of Mass Information strongly advises journalists to check such messages even if they do not appear similar to classic spam or malicious emails.
Here is to check the messages: do not follow suspicious links or enter any account data; before opening anything, check the URL using services such as VirusTotal and urlscan, and check the phishing databases such as PhishTank. It is also a good idea to confirm the authenticity of the invitation through another communication channel: if the message was received in Signal, you should not automatically consider it safe: Signal protects the message during transmission, but does not check the links and does not protect against phishing attempts overall. If in doubt, better check with the sender by phone or through the official event organisers’ official contacts.
