
Collage by the IMI
The Institute of Mass Information (IMI) received multiple phishing emails claiming to be from accountants, which arrived to the NGO’s inbox on April 8. The emails were sent by the hacker group UAC-0050, which is affiliated with the Russian intelligence services, as confirmed to the Institute of Mass Information representative Lesya Lutsiuk by the State Computer Emergency Response Team of Ukraine (CERT-UA).
The phishing emails had the name of the NGO listed in the subject line, which made them stand out from similar emails the IMI has received in the past. The emails included an attachment with link to a zip document containing malicious files. The emails were sent from different addresses, probably generated by software: [email protected], [email protected].
The emails sent to the IMI team are identical in content and structure, with the senders placing particular emphasis on the urgency of the letter. The letters were sent in quick succession, with a few minutes gap. Both emails were signed by a “chief accountant” addressing the IMI’s finance department with a demand to sign some documents and submit copies of them.
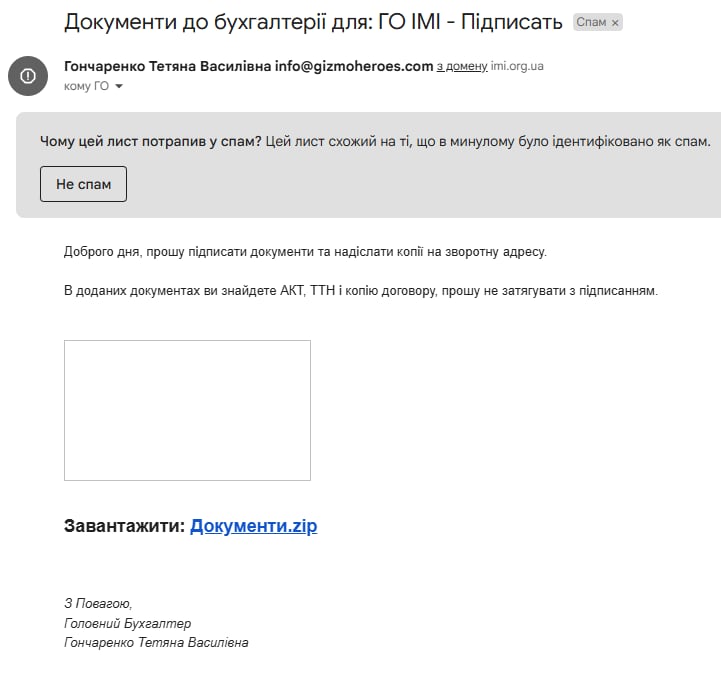
Screenshot of a phishing email that arrived to the IMI’s inbox
Digital Security Laboratory (Tsyfrolaba) tells the IMI that such emails aim to install malware that will spy on the victim and steal data from their computer’s Windows system.
Tsyfrolaba specialists explain that the archives sent by the hackers contain password-protected documents and the malicious file “Password.js”. If you run it on a computer with a Windows operating system, it will secretly install the software Remote Utilities, which can take screenshots, make recordings with the microphones and cameras, steal passwords, documents, etc.
“The Russians are closely monitoring and looking for weak points to gain access to journalists and activists. While in the past their emails used to be in Russian or a mix of languages, now they are improving the letters, writing them in Ukrainian and adding some details to create the impression that the email is authentic. However, all these letters have one style: a call to act urgently and a ‘document’ attached that has to be downloaded from another service. They hope that Ukrainians will download the document in a hurry and then the Russians will be able to access their accounts or monitor their devices remotely,” said Yana Mashkova, a media expert at the Institute of Mass Information.
In early 2025, Tsyfrolaba reported a surge in finance-related phishing attacks by Russian hacker groups, which likely target accountants, heads of organizations, and sole proprietors in order to install remote access malware.
The IMI has also reported that Ukrainian information systems are being targeted by hacker groups working as part of Russian intelligence services, and that some private hacker groups have also begun to work for the Russian state.
In the first year of the full-scale invasion, the IMI was targeted with a powerful cyberattack. The perpetrators tried to stop the IMI website from working through the newsletter subscription form. In 2023, the website sustained another DDoS attack and was down for more than an hour. The IMI believes the attacks to be retaliation for the NGO’s work such as documenting the crimes committed by Russia against the media and journalists.
In the three years and one month since the start of the full-scale invasion, Russia has committed 102 cyber crimes against the media and journalists. Learn more about digital threats and countering them in the “Cybersecurity” section, created as part of the Institute of Mass Information project “Jmama”.
