“Vilne Radio” has suffered a series of phishing attacks targeting the media outlet’s corporate email, reports the radio station’s executive director, Anastasia Shybiko, in a comment to the IMI.
According to Anastasia Shybiko, at least four suspicious letters with attachments that could be malware were sent to the station’s main inbox on August 5–16.
The first email arrived on August 5 and was signed “Solomyansky District Tax Inspection of the Kyiv Tax Service HQ”. Then, on August 9, two more letters from the “tax service” arrived from different e-mail addresses. On August 12, the outlet received an email from the “Main Office of the Security Service of Ukraine”, and on August 16 – one ostensibly from PrivatBank.
Shybiko stressed that these letters were sent to “Vilne Radio’s” main corporate inbox.
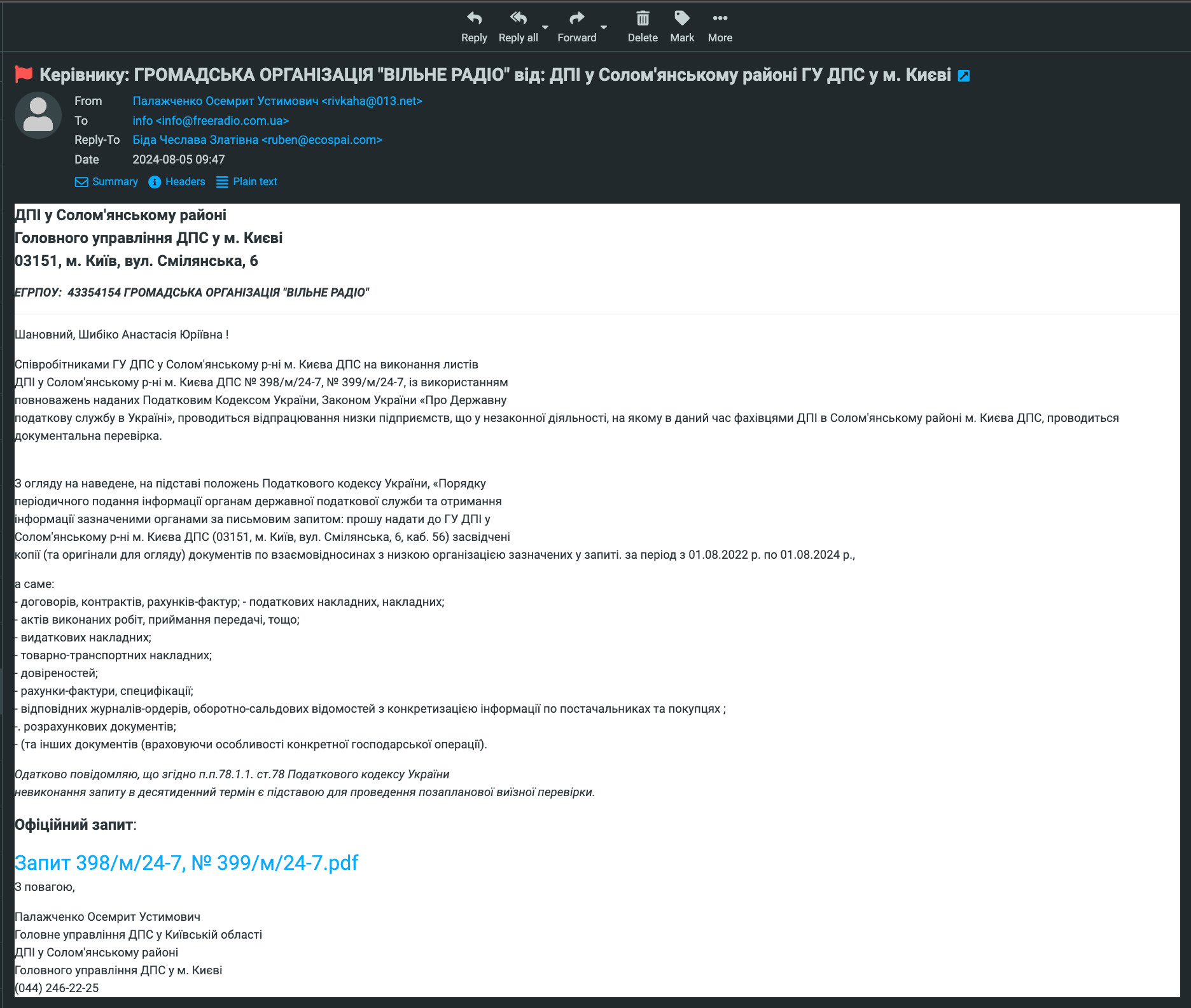
A phishing email “from the tax service” received by “Vilne Radio”
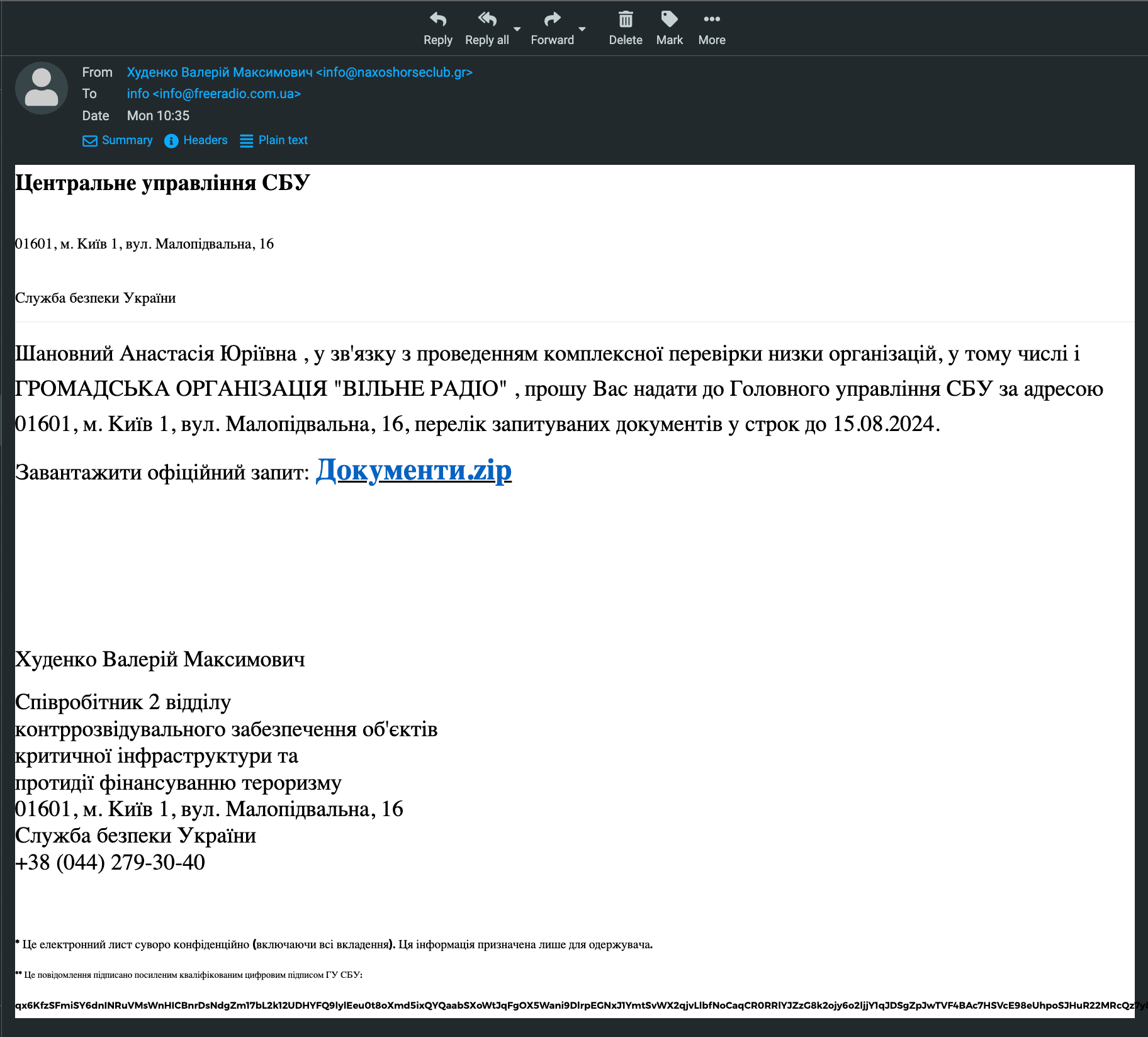
The phishing email “from the SBU” received by “Vilne Radio”
Anastasia Shybiko has received similar emails to her personal inbox as well, but paid them little attention.
All of the emails contained attachments that were recommended for download, which is typical of phishing attacks and suspicious.
“The suspicious addresses and names of the senders are not found through Google search, and the addresses clearly do not belong to the authorities mentioned in the letters,” Shybiko says.
In her opinion, the PrivatBank letter, where email address appears plausibly authentic, is the most suspicious, as it raises concerns about the bank’s security system.
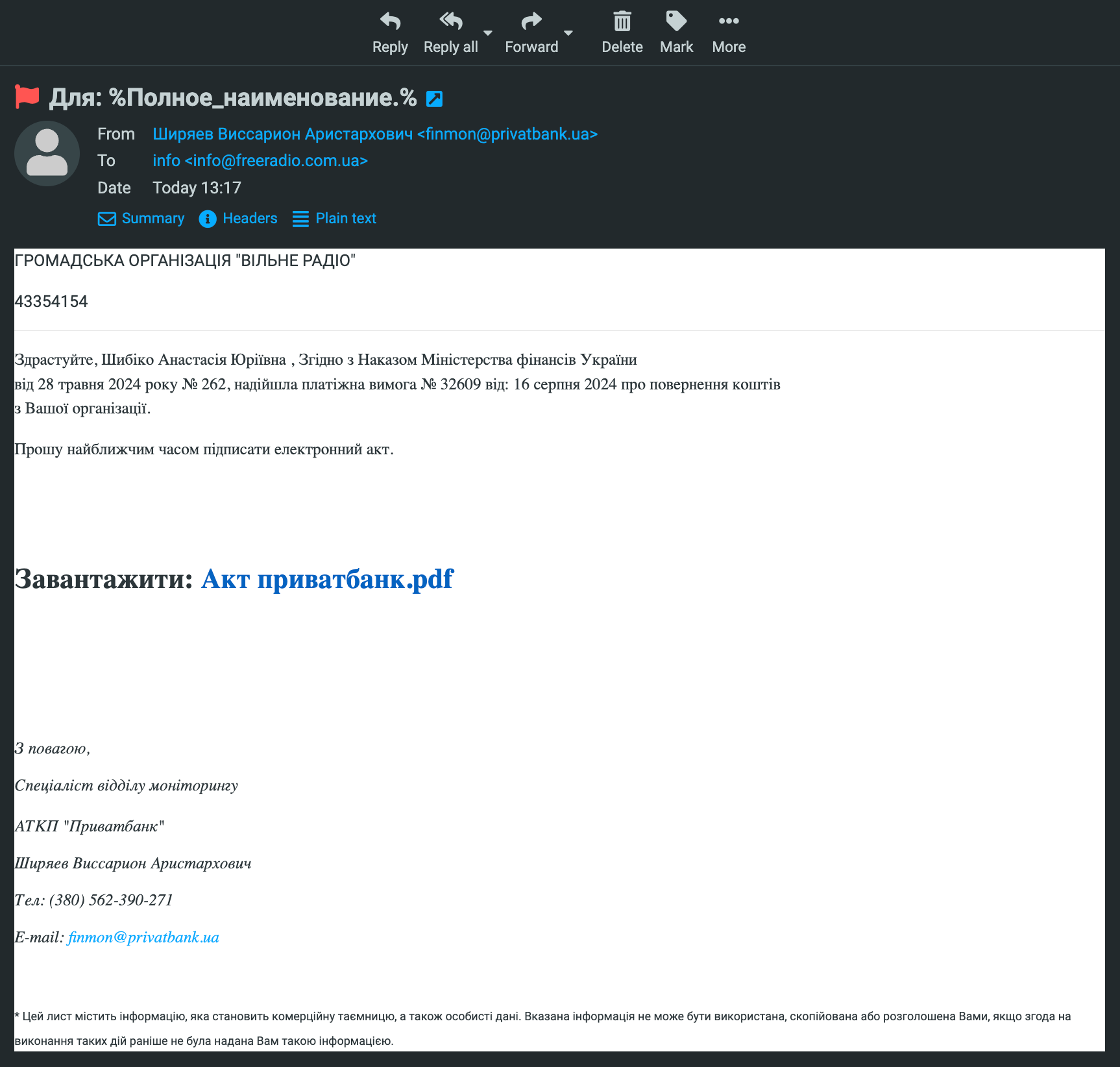
The phishing email “from PrivatBank” received by “Vilne Radio”
The “Vilne Radio” executive director notes that the emails often addressed her as the “head of the NGO Vilne Radio”, which is incorrect, and used multiple font sizes, while stressing that the message is strictly confidential.
“The Solomyansky STI has nothing to do with us, and the SBU’s demand to provide the NGO’s documents also sounds strange,” she added.
Anastasia Shybiko suggests that this phishing attack may be related to the activities of Russian cybercriminals, offended officials or simply trainee hackers trying to hack a website, e-mail or infect computers with viruses.
Earlier, hackers mimicked the Ukr.net website to steal email accounts.
The state computer emergency response team CERT-UA, operating under the State Special Communications Service, recorded attacks by the hacker group UAC-0102 in July. The hackers aimed to steal the Ukr.net accounts of government employees, military personnel, and employees of Ukrainian enterprises and organizations.
They attempted this by sending emails with attached archives containing an HTML file. After opening the file, the recipient would end up on a phishing website that mimicks the Ukr.net page. If they signed in with their login and password, the data would be sent to the hackers and a document would be uploaded to the victim’s computer to divert attention, noted the SSCS.



